Did you know that Symantec- An American Software Company discovered more than 246 million new malware variants in 2018?
Let’s be honest; no device is immune to malicious software or infections. They are a threat to your security terminology and can compromise your device functions. With the intent to exploit and damage your systems, devices, and networks, Malware can steal data and get access controls to harm the computers.
No matter how much you know about Malware or Malware removal, it is essential to get its classification straight to stop or remove them.
Mobile PC Medics, in this regard, is a virus removal professional service that effectively performs virus removal to keep your devices secure. The malware specialist offers you fantastic antivirus advice to keep the threat of damaging Viruses and Malware at bay.
Let’s get into the details to determine more about the various types of Malware and how to detect and remove them.
Table of Contents
Malware and Its Types- An Overview
Malware typically refers to malicious software. The umbrella term comprises worms, viruses, Trojans, and several other harmful programs. Hackers and spammers use these malicious programs to damage your data and, more importantly, gain access to confidential and sensitive information.
Microsoft defines Malware as any software that causes damage to your computer network, server, or computer. Experts identify Malware as software that tends to harm a system or damage it rather than a particular technology or technique used to design it.
Types of Malware
Interestingly, you can pigeonhole Malware in plenty of categories. Generally, it depends on how fast malicious software can spread. People often use worm, virus, and Trojan interchangeably; however, the three forms are subtly different when infecting the systems. According to Symantec;
- A virus is basically a form of computer code that has the ability to insert itself within other standalone program’s code. It not only leads the program to perform malicious activities but also spreads quickly.
- A worm is also malicious software that spreads itself by reproducing itself. It can infect multiple devices at the same time.
- On the other hand, a Trojan doesn’t reproduce like a worm and virus, but it can trick users into something they are looking for. Once clicked, the Malware activates, damages the system, and spreads quickly.
Manually Installed Malware
Attackers and hackers can also install the virus manually on devices and computers. They can do it if they gain physical access to the system or use privilege escalation for remote administrator control. It is sometimes more harmful than the automatic codes and programs infecting your computers.
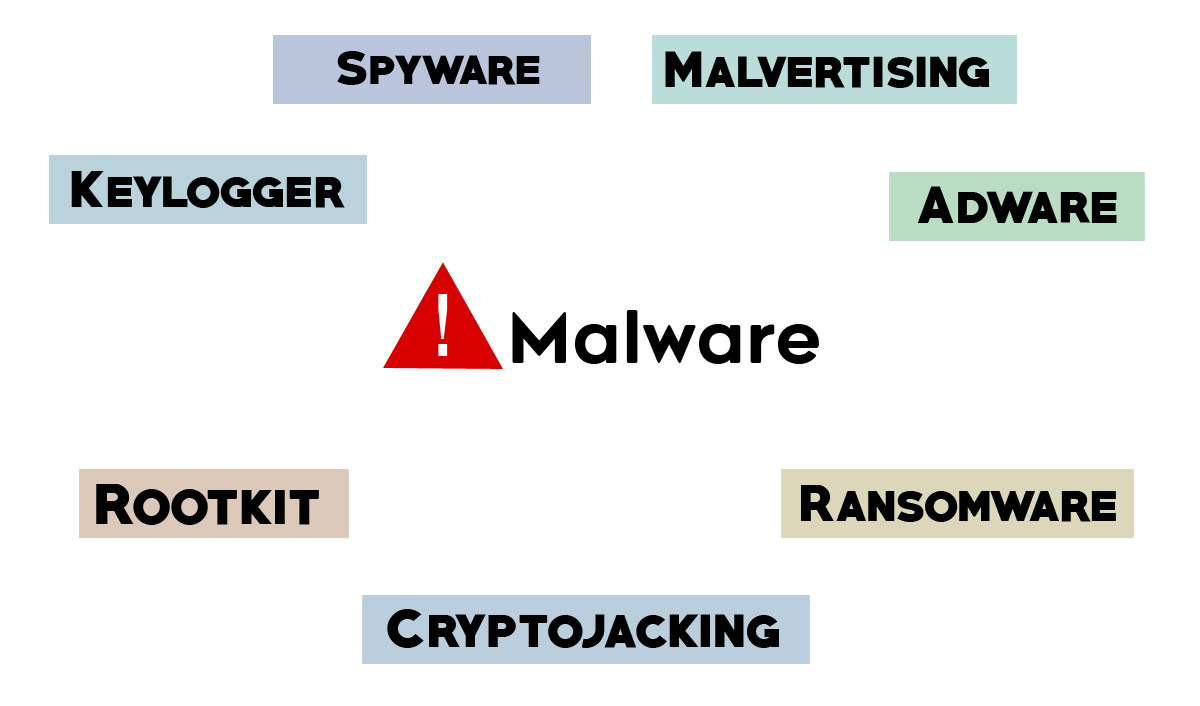
Here is a breakdown of some of the most common manually installed Malware your computer may have;
» Spyware
According to Webroot Cybersecurity, most unsuspecting users become the victim of “Spyware.” A hacker installs on the system to secretly collect the data. Typically, it has a purpose to spy on activities you do on your computer or other devices. It gathers the data you exchange with your peers and sends the information to a third party.
» Keylogger
If someone steals your password using Malware, he/she might use a “keylogger,” which is specific spyware. It can record the keystrokes to copy the details of your password.
» Rootkit
A rootkit is another type of manually installed Malware that can shift the remote access and control from one computer to another. TechTarget defines this Malware as a set of software tools that can gain root access, such as administrative level control over the other system and the presence.
» Adware
Adware is another common malware that redirects the ads on the web by forcing the browser. It further leads the users to download various ads that have more viruses and malicious software. New York Times mentioned that the software tempts users with free games, browser extensions, and programs.
» Ransomware
Ransomware, as the name implies, encrypts the files in the hard drive. The attacker or hacker demands money in exchange for the system’s description key. You might have seen many malware outbreaks, such as Petya ransomware, which infected numerous companies and businesses.
If you don’t access your description key, it is mathematically challenging to regain access to your data and files.
Scareware is another version of this Malware that claims the control your device or computer for ransom. However, it uses different browser loops to masquerade more damage than it does.
» Cryptojacking
Cryptojacking is crypto mining malicious software that infects computers and uses them to mine Bitcoin. It is one way to get the attacker’s profit. An attacker runs this mining software in the background on the system or in the browser window without you knowing.
» Malvertising
The malware type uses legitimate ads to infect the computers. For instance, a cybercriminal pays to run an ad on an authentic website, and when you click on the ad, it redirects you to a malicious site. It may also install various Malware and virus on your computer.
Sometimes, the malicious software executes itself automatically without having you click anything. This is a drive-by download.
How can you Detect and Prevent Malware
Phishing emails are the primary reason for malware infections on computers. It is crucial to make sure that you lock down your email system tightly. Plus, your users must be aware of how they can spot malicious viruses.
They should carefully check all the attached documents and restrict behavior. Also, you can take some technical measures to protect your system. Patching, updating, and performing vulnerability assessments on your digital infrastructure are some ways to secure your data.
Use hi-tech visibility tools to detect unfamiliar activities on your network. They can help you detect malicious software and indicate if there is a malware infection.
Malware Removal
Viral removal or malware removal is a challenging business. The methods may vary depending on the type of malware that has infected your computer. It is always better to consult pros like Mobile PC Medics to recover from malicious software like Cryptojacking, rootkit, and ransomware.
Mobile Pc Medics – Why We Are Professional
Leading computer services work with a team of professionals who rely on special programs for virus or malware removal. They safely perform virus removal and help you get rid of spyware and underlying rootkit virus problems.
We have experienced and competent techs that efficiently remove mobile viruses and offer you the best protection advice to keep your devices safe in the future. We understand how fake antivirus programs can damage your computer system, causing you to lose money or functionality.
At Mobile PC Medics, we have a team of experts who can detect and remove malware from your computer.
Contact our viral removal services at 818-307-6868 or visit our website today if you live in Newbury Park, Agoura Hills, Hidden Hills, Camarillo, West Hills, Thousand Oaks, Calabasas, or Oxnard.
